Computers around the world are infected. What happened?
On Friday, May 12, 2017, a massive cyberattack called WannaCry took place globally, affecting millions of computers, thousands of companies and agencies, and catching most of the world totally off guard. This brand of hack falls under the category of ransomware, which you can learn more about here.
Whereas some hackers want to break into networks and computers, do their damage and then walk away quietly, ransomware is just the opposite. The hackers make it a point to tell you they’re in your network or computer. And they demand money.
A global hack attack!
More than 150 countries were affected, including China, Great Britain, Russia, the United States and the Middle East. Millions of computers were being held for ransom at the same time. The ransomware attacked computers belonging to businesses, governments, and institutions such as hospitals, schools, transportation companies and police stations.
The WannaCry ransom message is straightforward: pay the hackers a specific amount of money or you’re going to lose important files and documents on your computer. Using ransomware (a type of software virus), hackers freeze the files in computers system, denying the user access to those files until a ransom is paid. However, there’s no guarantee the hackers will keep their word.
Here are answers to basic questions about the WannaCry Ransomware attack.
How did the malware get on all those computers?
The WannaCry malware was launched globally and affected computers that were using a version of the Windows operating system that had a vulnerability to viruses. Microsoft Corp. had made a patch (or fix) available for users a few months ago, but millions of computers worldwide had not been updated with the correction or their owners were unaware of the issue. The hackers exploited the flaw.
Could the WannaCry ransomware affect my computer?
If you haven’t seen it yet, then it’s not likely. There could be future waves of WannaCry or a similar version of it. Also, it seems WannaCry was directed at mostly larger organizations. However, you could be affected by another strain of ransomware at any time.
How widespread was it?
The reach was indeed global. More than 150 countries were affected, including China, Great Britain, Russia, the United States and the Middle East. Millions of computers were being held for ransom at or around the same time. The official media for China reported that more than 29,000 “institutions” had been affected and hundreds of thousands of Internet-connected devices. In Japan, 600 different locations and 2,000 computers were hit. Hospitals in Jakarta, Indonesia had their patient files held for ransom, causing serious delays. The impact was greater in Europe and Asia than the West.
How did people discover their computer was infected?
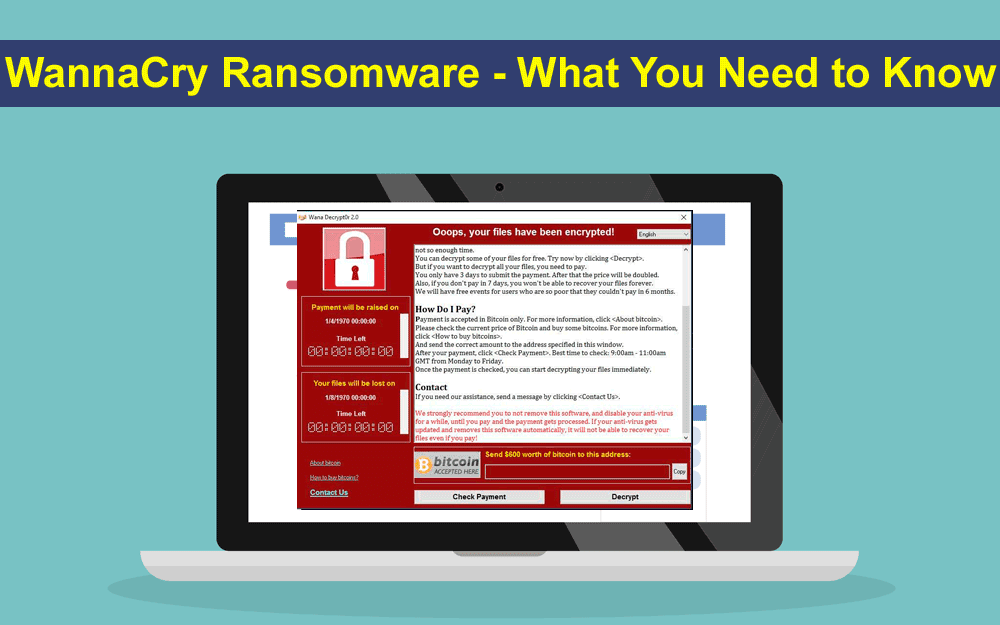
When victims opened their computers (and if it was infected) they saw a frightening screen message that said “Oops, your files have been encrypted!” The screen message showed how much time they had in order to pay up, the amount of the ransom (to have access to the files again), and instructions on how to pay the ransom demand.
Who did it?
Nobody knows with certainty who did it. A handful of days after the attack, law enforcement agencies and coalitions from around the world had not identified the culprit or culprits and they hadn’t come forward to claim responsibility. That’s why online cyberterror and crime is so dangerous: hackers—many who are sophisticated network/technical experts—can attack and stay hidden in the shadows of the Internet.
How long did the attack last?
Thankfully, not very long. Here’s why: A few days after the attack, a security researcher with a private company noticed a strong similarity between the WannaCry malicious code and malware created and used once before by a well-known hacking operation, called Lazarus, which has links to North Korea. Information is changing quickly as more details become known daily. It’s ironic that as ransomware spreads, so do does the investigation
Did people pay the ransom demands?
It doesn’t seem that the WannaCry hackers made a lot of money, if that was their primary intention, although the facts aren’t known. According to news reports, a very small number of companies and computer-users affected (and there were millions!) paid the demands. Police agencies advise victims not to pay ransomware demands.
How much were the hackers asking for?
Reports indicate the ransom message was asking individual computer users for $300 right away, then upping the ransom demand to $600 just hours before the files were to be deleted. If that seems “small” in price, remember that millions of users were being attacked and millions of computers were being held ransom at one time by the same ransomware! The victims were supposed to send the ransom using Bitcoin, a digital, Internet-based currency.
What were some of the companies that were attacked?
Same very well know companies and organizations from around the world were victims of the WannaCry attack. In the Unites States, FedEx delivery company reported they were experiencing interference with some of their Windows-based systems caused by malware,” but they didn’t reveal the impact. In the UK, many hospitals hit by WannaCry had to cancel appointments and operations. Doctors reported not being able to send important emails about patients. Car manufacturers, Renault (France) and Nissan (Japan), both reported attacks. Germany’s biggest train system was hit and Russian banks were also attacked.
Was the WannaCry attack stopped?
Yes, and no. According to news reports, a researcher who works for a private security firm in the U.K. did some online detective work and was able to find an online solution. He triggered a “kill switch” that turned the malware off. (In a way, he found a flaw in the malware.) His actions helped stop the spread the virus, but it didn’t do any “decrypting” of the already infected computers. Despite his actions, security experts think the perpetrators could still release another strain of the ransomware virus that doesn’t have the kill switch.
Is there anything we can do to protect ourselves from WannaCry?
Most computers infected were connected to networks that had a vulnerability in their Microsoft operating systems. If you’re connected to such a network (at work, for example), there’s little you can do on your own to protect yourself.
In general, however, you can avoid ransomware by making sure you’re using the most updated version of your Windows operating system; that you’ve installed all “patches” or corrections Microsoft has sent on your version of Windows; that you immediately install patches when you get them; and that you have a good antivirus program that can alert you to a problem.
Sources: Los Angeles Times, Editorial/Opinion, May 16, 2017; Wall Street Journal, May 15, 16 editions.
CBC/Radio-Canada, www.cbc.ca/news/technology, May 15, 2017.